

Increasing connectivity brings many advantages, but also some disadvantages, as the rise in cybercrime shows. Cyber criminals have the opportunity to install malicious code on users' computers as a result of programming errors.
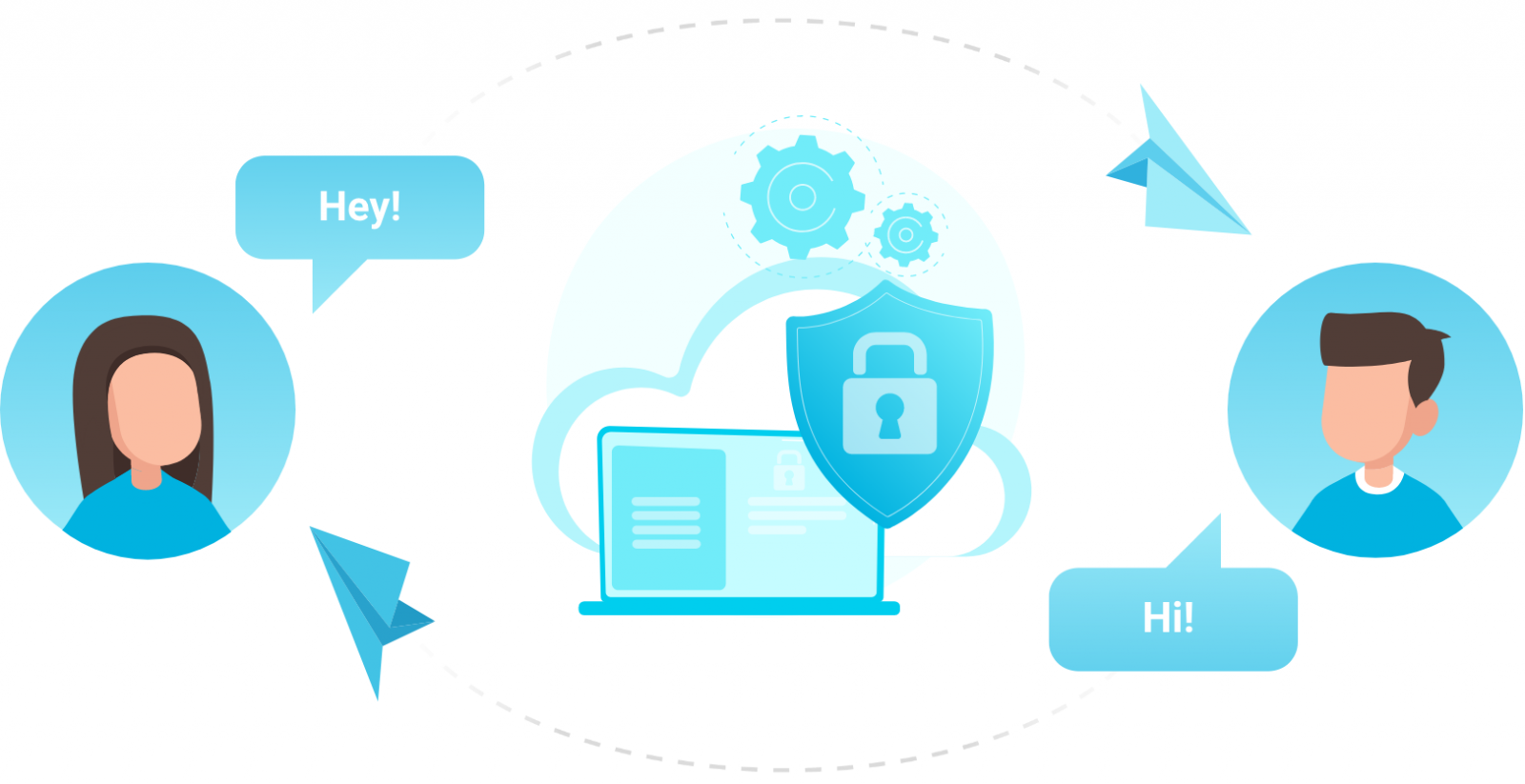
With the ever-increasing use of the Internet in the wake of digital transformations, information security must be ensured, as well as protecting people from cyberattacks. For this reason, a security solution called end-to-end encryption was developed to ensure encrypted information exchange between two communication partners. This prevents intervention by third parties.
What is end-to-end encryption?
The abbreviation "E2EE" stands for "End-to-End Encryption". In this process, the sender encrypts the transmitted information and only decrypts it again once it reaches the intended recipient. The data remains encrypted over the entire transmission path. Third parties, such as service providers, have no access to this content, apart from control information used to ensure that the encrypted information is forwarded.
How does the process take place?
Various cryptographic procedures are used here, such as symmetric or asymmetric encryption with public and private keys. This procedure of asymmetric encryption is called "Public Key Encryption". The public key of a communication partner A is accessible to everyone. Data encrypted with a public key is decrypted only with the corresponding private key. Only communication partner A has access to the private key.
The protection of digital identities
Since 2010, Germany has had the online ID function, which serves to better protect users. Digital identity verification is a major advancement needed in this digital world. The identify platform ensures this protection. The video conferencing function is BaFin-compliant and meets the legal guidelines. The identify platform was programmed with end-to-end encryption. All data is secured in encrypted form on German Norisnetwork servers.
- Wir melden uns bei Ihnen -